Important News:SafeLogic Announces General Availability of CryptoComply BoringCrypto! Read the announcement.
Post-Quantum Ready Cryptography & Encryption for Financial Services
Financial institutions are the #1 target for quantum threats and Harvest Now, Decrypt Later (HNDL) attacks. SafeLogic delivers validated, interoperable, production-ready cryptographic software that strengthens your security foundation today and prepares your organization for PQC tomorrow.
Financial Cryptography & Data Security
Cryptography is the invisible backbone of modern finance. Every transaction, login, data exchange, API call, and mobile session relies on strong, reliable, and properly implemented encryption.
Financial institutions depend on cryptographic software to secure:
- Mobile and online banking experiences
- Payment systems, ACH/Fedwire/SWIFT workflows, and card transactions
- API and microservices architectures powering digital banking and fintech ecosystems
- Digital identify, authentication, and customer access systems
- Trading platforms and proprietary algorithms
- Customer communications, statements, and document exchanges
- Data at rest, in motion, and in use across cloud, hybrid, and on-premise environments

As financial institutions adopt Zero Trust architectures, cryptography becomes even more central.
Zero Trust depends on continuous authentication, encryption by default, and strong key management—all of which require modern, validated, and interoperable cryptographic software.
The Financial Industry Is Facing Unprecedented Threat Levels
Financial institutions are the most targeted sector in the world, facing nation-state adversaries, organized cybercrime, and increasing volume of long-term data harvesting attacks. Three factors make financial services uniquely vulnerable:
#1. Constant and Sophisticated Attacks
Financial institutions endure the highest volume of sophisticated cyberattacks globally, fueled by the value of financial data and the constant attempts to exploit real-time transactions and digital banking platforms.
#2. Long-Retention,
High-Value Data
PII, transactions, wealth management records, and insurance data often must be stored for years or even decades, making them prime targets for “Harvest Now, Decrypt Later” strategies.
#3. Expanding Digital Footprints
Mobile apps, APIs, cloud adoption, and fintech integrations create a large cryptographic attack surface that adversaries are actively collecting today to decrypt once quantum capabilities mature.
Classical Cryptography is Under Threat from the Emergence of Quantum Computers
For more than 30 years, the security of digital finance has depended on asymmetric (public/private key) cryptography, including the RSA and ECC algorithms used in TLS, PKI, digital signatures, authentication, mobile banking, APIs, payment systems, and nearly every secure interaction across financial infrastructure.
These classical algorithms rely on mathematical problems that are infeasible for traditional computers to solve. However, advances in quantum computing fundamentally change that equation.
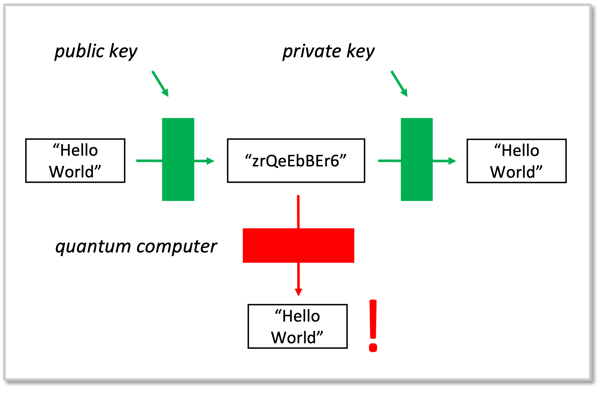
Quantum Computers will Break Today’s Public-Key Cryptography
The quantum algorithms demonstrated by researchers, including Shor’s algorithm, will eventually allow quantum computers to solve the underlying mathematical problems that keep RSA and ECC secure today.
In other words: Once large-scale quantum computers arrive, the cryptography that protects financial systems today will no longer be secure.
This is not a distant speculation—timelines are accelerating:
- Gartner predicts that quantum computers will render current cryptography systems unsafe by 2029.
- Many financial institutions maintain sensitive data for 7 – 30+ years, meaning sensitive information encrypted today may be decrypted in the future.
- Cryptographic modernization cycles in banks often take 3 – 7 years, requiring action well before quantum systems mature.
Even Without Quantum Computers Today, 'Harvest Now, Decrypt Later' is Already a Critical Threat to the Financial Services Industry
Quantum computers don’t need to exist at scale for financial institutions to be at risk today. Adversaries are already engaging in Harvest Now, Decrypt Later (HNDL) attacks, quietly collecting encrypted financial data now with the intention of decrypting it once quantum capabilities mature. This is especially perilous for the financial sector, where encrypted data retains value for years or decades.
Why Financial Institutions Are Prime Targets for HNDL:
- Extremely sensitive, high-value data. Customer PII, account details, transaction logs, and payment data remain valuable indefinitely.
- Long retention requirements. Regulatory and audit frameworks often require data to be stored for 7 – 30 years, well within the quantum risk window.
- Operational and systemic impact. Decryption of historical transaction data or authentication records could compromise trust, integrity, and downstream systems.
- Regulatory exposure and reputational risk. A quantum-enabled breach of historical data would trigger significant compliance consequences and loss of confidence.
- Proprietary and competitive information. Trading strategies, actuarial models, and financial algorithms hold long-term strategic value.
The Risk is Immediate
Because encrypted financial data collected today may be decrypted in the future, the threat already exists. Quantum-resistant and hybrid cryptography are essential to ensure that long-lived data and communication channels remain secure now and for decades.

Financial Institutions Are Already Migrating to Post Quantum Cryptography

All signals point in the same direction: Financial institutions cannot wait for quantum computers to arrive before acting.
Transitioning from classical cryptography to PQC isn’t a simple upgrade. It is a multi-phase effort that touches infrastructure, applications, and governance.
To maintain trust, privacy, and security during the quantum transition, financial institutions must adopt crypto-agile architectures and begin deploying PQC and hybrid/classical PQC algorithms well before quantum computers arrive.
What Financial Institutions Need to Protect
Financial institutions operate some of the most complex and interconnected digital ecosystems globally. As quantum threats and HNDL attacks grow, every cryptographic touchpoint that handles sensitive or long-lived data becomes a potential exposure point.
To stay secure today and resilient tomorrow, financial organizations must prioritize quantum-ready protections across:
Mobile platforms represent the fastest-growing attack surface in financial services. They rely heavily on:
- TLS sessions
- API calls
- Client-side encryption
- Digital identity workflows
These encrypted channels are top targets for data interception and long-term harvesting.
API-first and microservice architecture power modern digital banking and fintech integrations.
Each service-to-service connection depends on:
- TLS encryption
- Key establishment
- Mutual authentication
Compromise of these encrypted communications puts entire business ecosystems at risk.
ACH, Fedwire, SWIFT, card transactions, and real-time payment systems all use cryptography to ensure:
- Integrity of financial messages
- Confidentiality of transaction data
- Authentication of endpoints and systems
These workflows often have long-term analytic or compliance value, making them highly vulnerable to HNDL threats.
Financial institutions maintain massive volumes of long-lived records:
- Customer PII
- Historical statements
- Long documents
- Wealth and pension data
- Insurance records
- Regulatory archives
Much of this data must be stored for 7 – 30+ years, putting it at an elevated risk of future quantum decryption.
Public-key cryptography underpins:
- Customer authentication
- Employee and administrator identity
- Access control
- Transaction signing
- Certificate-based workflows
Since these systems rely heavily on RSA and ECC, they must transition to PQC and hybrid digital signature algorithms to ensure future security.
As workloads shift to AWS, Azure, GCP, and containerized platforms, cryptography becomes distributed across multiple environments. Each requires validated, inoperable, and crypto-agile cryptographic software for:
- Key management
- TLS encryption
- Service authentication
- Data-at-rest encryption
Archived financial data, whether stored in the cloud, on-premises, or on tapes, remains valuable for decades. This makes it a prime target for harvesting, even if attackers cannot break its encryption today.
Any data with long-term value must be protected with hybrid PQC or PQC-ready cryptography now, before adversaries collect it.
The bottom line: The quantum transition will impact every encrypted connection, record, transaction, and identity workflow. Financial institutions must begin securing these critical systems immediately, not just to meet emerging requirements, but to protect the long-lived data that defines the industry.
Assess Your PQC Readiness
Financial Firms Must be Crypto-Agile
PQC migration will happen in phases—and financial institutions cannot afford to rebuild every application, library, and dependency each time standards evolve. Crypto-agility is now a foundational requirement for financial infrastructure. But true crypto-agility requires more than swapping algorithms.
Crypto-Agility Requires:
- Enterprise-wide visibility into what cryptographic algorithms, key sizes, libraries, and versions are actually in use
- A centralized policy layer to enforce cryptographic standards across apps, services, mobile, cloud, and legacy systems
- A cryptographic SBOM/CBOM that continuously tracks changes and protects against supply-chain vulnerabilities
- The ability to upgrade cryptography without rewriting applications.
- A controlled migration path from classical → hybrid → full PQC
Financial institutions already know the cost of not having this visibility—Log4j exposed how fragile and opaque software supply chains really are. Cryptography is no different. In fact, its sprawl is worse.

Hybrid PQC: The Practical Step for Financial Institutions
The transition to post-quantum cryptography will take years, and it cannot be done in a single jump. To protect long-lived financial data during the transition period, global cybersecurity agencies, including NIST, NSA, and NCSC, recommend deploying hybrid classical/PQC algorithms.
Hybrid PQC combines traditional cryptography (such as RSA and ECC) with quantum-resistant algorithms (such as ML-KEM) in a single handshake. If either algorithm is ever compromised, the other still protects the session.
Why Hybrid PQC Matters for Financial Institutions
- Protects against HNDL. Even if classical cryptography is broken in the future, quantum-resistant components prevent past session data from being decrypted.
- Modernizes TLS for banking, payments, and APIs. TLS is the backbone of mobile banking, ACH, SWIFT APIs, web banking, and fintech integrations. Hybrid PQC strengthens these critical channels without service disruption.
- Enables crypto-agility at scale. Financial organizations can deploy PQC gradually, system-by-system, without breaking legacy integrations.
- Supports Zero Trust architectures. Strong, future-proof cryptography is foundational for identity, authentication, and secure access.
- Ensures interoperability during multi-year transition cycles. Classical and PQC algorithms work together so institutions can upgrade infrastructure without downtime or rewrites.
SafeLogic Cryptographic Software & Enterprise Support for Financial Institutions
Financial institutions often discover that cryptography is woven through every layer of their infrastructure—mobile apps, APIs, cloud workloads, internal services, legacy platforms, authentication systems, payment rails, and archival storage. Many banks rely on a patchwork of cryptographic libraries, each with different configurations, risk profiles, and maintenance challenges.
SafeLogic helps financial institutions simplify these processes.
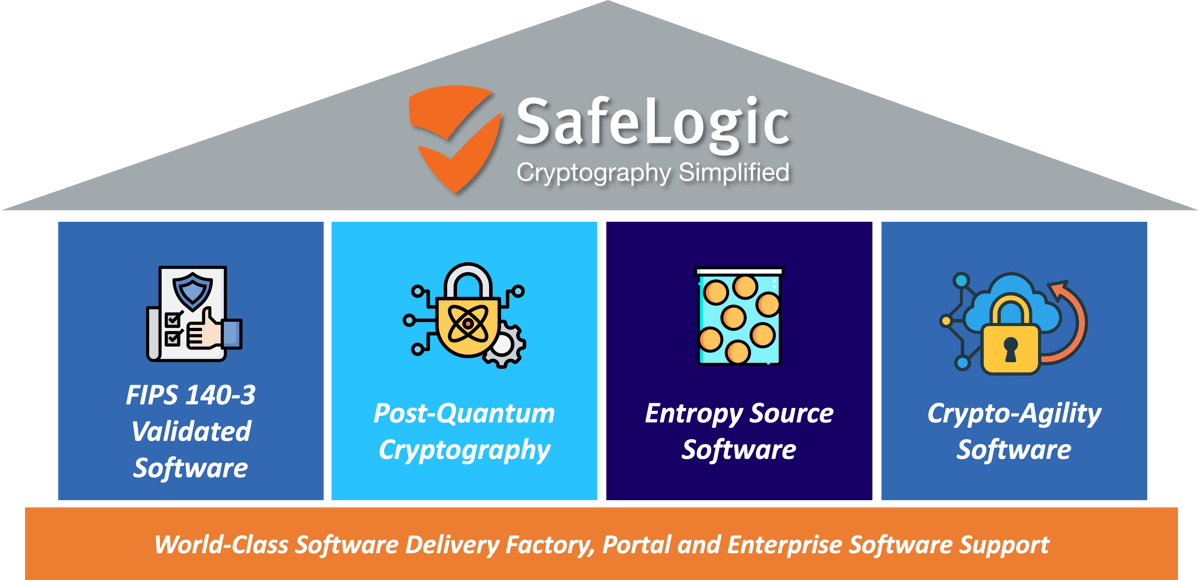
SafeLogic provides a unified cryptographic foundation built for enterprise scale—combining FIPS 140-validated software, post-quantum cryptography, high-assurance entropy, and crypto-agility tooling into a single, interoperable platform.
Our world-class software delivery factory ensures consistent, high-quality releases across all supported languages and environments, while our enterprise support and portal give financial institutions the visibility, control, and assurance they need to modernize cryptography across their entire infrastructure. SafeLogic replaces fragmented libraries with a consolidated, validated, and quantum-ready approach designed for long-term resilience.
Standardize Cryptography Across the Enterprise
SafeLogic’s CryptoComply cryptography software is engineered for enterprise-wide interoperability, eliminating the complexity of managing multiple cryptographic libraries. It helps financial organizations replace fragmented cryptography with a unified, validated, and quantum-ready foundation.
CryptoComply works seamlessly across:
- Cloud platforms: AWS, Azure, GCP
- Server ecosystems: Linux, enterprise databases, internal systems
- Application stacks: Java, Go, .NET, Python, C/C++, mobile SDKs
- Microservices & APIS: containerized services and multi-cloud workloads
- Mobile banking apps: iOS and Android

By replacing fragmented libraries with a single drop-in compatible solution, financial institutions:
- Reduce operational risk
- Simplify audits and compliance
- Accelerate cryptographic modernization
- Improve engineering efficiency
- Eliminate dependency fragmentation
This is especially valuable for large banks where dozens of teams may each use different cryptographic components without central oversight.
SafeLogic Works with Your Entire Environment
Mobile • Web • API Gateways • Core Banking Systems • Cloud • On-Premises • Hybrid • Containerized Workloads • Java • Go • .NET • C • C++ • Mobile SDKs TLS • PKI • Digital Signatures • KMS Integrations
SafeLogic’s Hybrid PQC-TLS Capabilities
SafeLogic delivers hybrid PQC capabilities designed specifically for enterprise and financial environments, including:
- Hybrid classical/PQC key establishment (ML-KEM + classical algorithms)
- PQC-enhanced TLS for APIs, mobile apps, and payment systems
- Drop-in compatible cryptographic software (no code rewrites)
- Policy-driven crypto-agility to manage gradual PQC rollout
- Enterprise support to help guide your team and interconnected systems
Hybrid PQC enables financial institutions to act now and secure long-lived data, protect critical TLS channels, and prepare infrastructure for the complete PQC transition ahead.
Want to know more about how SafeLogic cryptography solutions can help your financial services firm? Speak with one of our experts!
Call us at 844-436-2797 or complete the form below.
PQC Readiness Is Operational: Move Beyond Discovery
February 24, 2026 • SafeLogic
CISA Takes a Major Step Toward Post-Quantum Readiness
January 28, 2026 • Alex Zaslavsky
SafeLogic Welcomes Scott Raspa as Chief Marketing Officer
January 28, 2026 • SafeLogic
Advancing Hybrid Signatures Toward Standardization
November 10, 2025 • Alex Zaslavsky
CryptoComply Java v4.5 with PQC Algorithms Now Available
October 6, 2025 • Evgeny Gervis



.png?height=630&name=Automated-Discovery-and-Remediation-of-Quantum-Computer-Vulnerable-TLS-Libraries%20(1200%20x%20628%20px).png)
.png?height=630&name=PQC-readiness-is%20operational-move-beyond-discovery-safeLogic-blog-post%20(1200%20x%20628%20px).png)

.png?height=630&name=CISA%20Takes%20a%20Major%20Step%20Toward%20Post-Quantum%20Readiness%20Blog%20Post%20(1200%20x%20628%20px).png)




%20is%20Now%20a%20Competitive%20Advantage%20for%20Tech%20Vendors%20(Website).png?height=630&name=Why%20Post-Quantum%20Cryptography%20(PQC)%20is%20Now%20a%20Competitive%20Advantage%20for%20Tech%20Vendors%20(Website).png)


